GATE [ Graphic Access Tabular Entry ]
An Interception-resistant Authentication And Encryption System And Method
Videos :
|
 GATE demo starts at 29:20 |
 Risk Roundup Interview |
Field Of The Invention
The present invention relates to authentication and encryption systems and methods. More particularly, to interception-resistant authentication and encryption systems and methods.
Background Of The Related Art
In modern society, daily life requires the use of a wide variety of information devices, such as mobile phones, PCs, notebooks, and ATMs to name a few. The information devices often keep users' personal data. Due to the importance of protecting this personal data, there are methods to securely lock and unlock these devices.
At present, the most commonly used method to lock and unlock these devices is a password-based challenge authentication procedure, whereby a device typically requires that, before accessing its services, users enter a user id and a password for identity recognition. This is known as a login. This login process is designed to prevent users' personal data from being stolen or fraudulently changed.
With the rapid daily increase of network coverage and accessibility, hackers are more likely to target users' passwords to gain access to their private information. In addition, hackers are becoming more and more sophisticated in guessing and cracking users' passwords. Therefore, simple passwords no longer provide adequate protection from cyber threats and espionage.
In view of this, various mechanisms have been implemented to provide better protection. For example, users are required to create a password that meets the requirements of password length, complexity, and unpredictability, such that the strength of the password is, in theory, sufficient enough to fend off brute-force search attacks and dictionary attacks. Furthermore, users are required to change their passwords regularly to invalidate old passwords, thereby reducing the chance that their passwords will be cracked. These mechanisms do enhance security to a certain degree and thus help users protect their accounts.
However, each organization may have a different set of password rules. Some require the password length to be at least 6 or 8 characters. Some require the use of mixed uppercase and lowercase letters, as well as numbers. Some require at least one special character, yet some do not allow special characters. When you think you have just created a very strong golden password (which you can use in all places), you will soon discover that your golden password is invalid in places with a different set of requirements.
As a result of these different password rules, it may be difficult, if not impossible, for users to remember the multitude of passwords they have set up with different sites/organizations. Thus, users will typically store their passwords in a file that is stored on their information device and/or in a password storage application that runs on their information device. The stored passwords can be targeted by hackers, and if they gain access to the device on which the passwords are stored, they will gain access to all the passwords and have access to all of the user's password protected accounts/sites. Therefore, implementing strict rules for passwords to avoid passwords that are too weak can have the opposite of the intended effect (an increased risk of exposing more information).
In addition to the restrictions of above, traditional password is prone to peeking, wiretapping, keylogging and phishing.
Purpose Of The Invention
The intention of this invention is to prevent passcode [ similar to traditional password, but can include symbols ] from being intercepted during the process of entering and transmitting. With the protection of the invention, user will not be afraid of being watched by a hacker while entering the information, because the hacker will not know the passcode. Even after many times of observing/intercepting the user entering the login info, the hacker will still remain unable to figure out the passcode.
Introducing The GATE [ Graphic Access Tabular Entry ] System
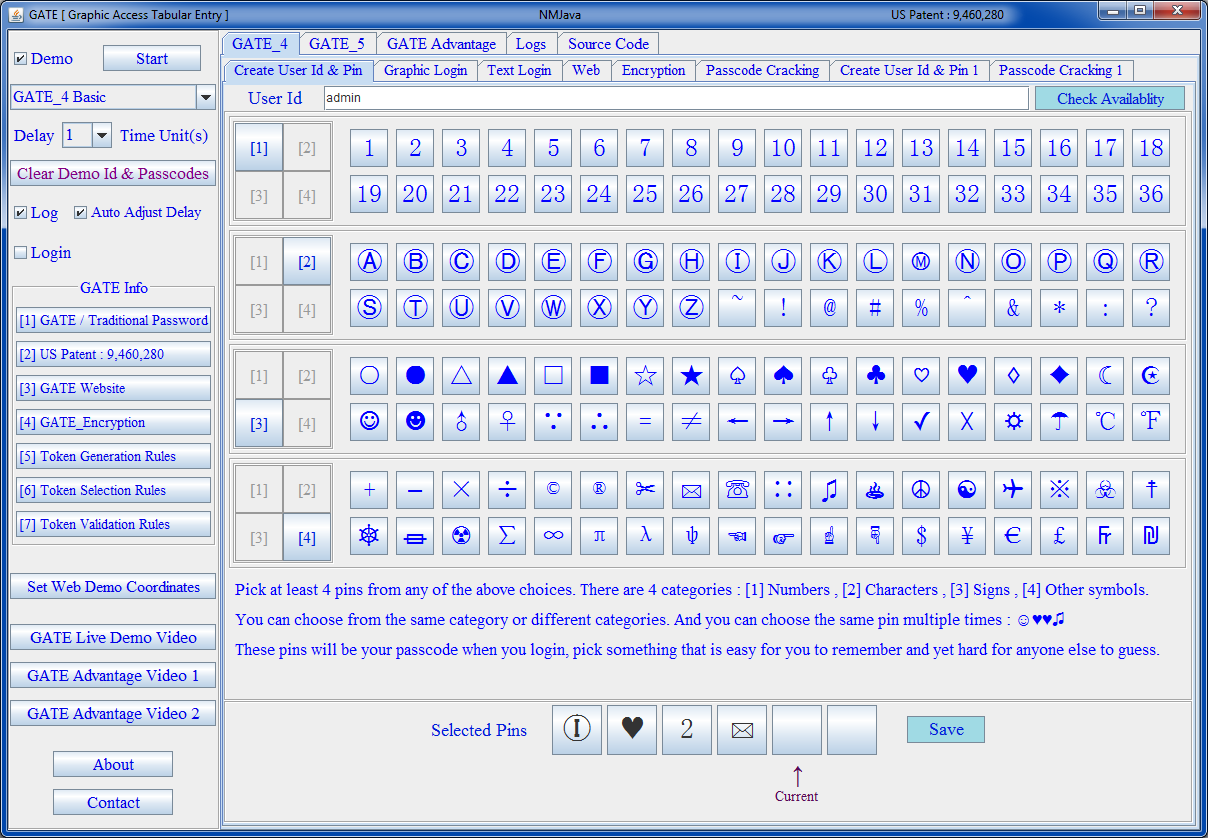
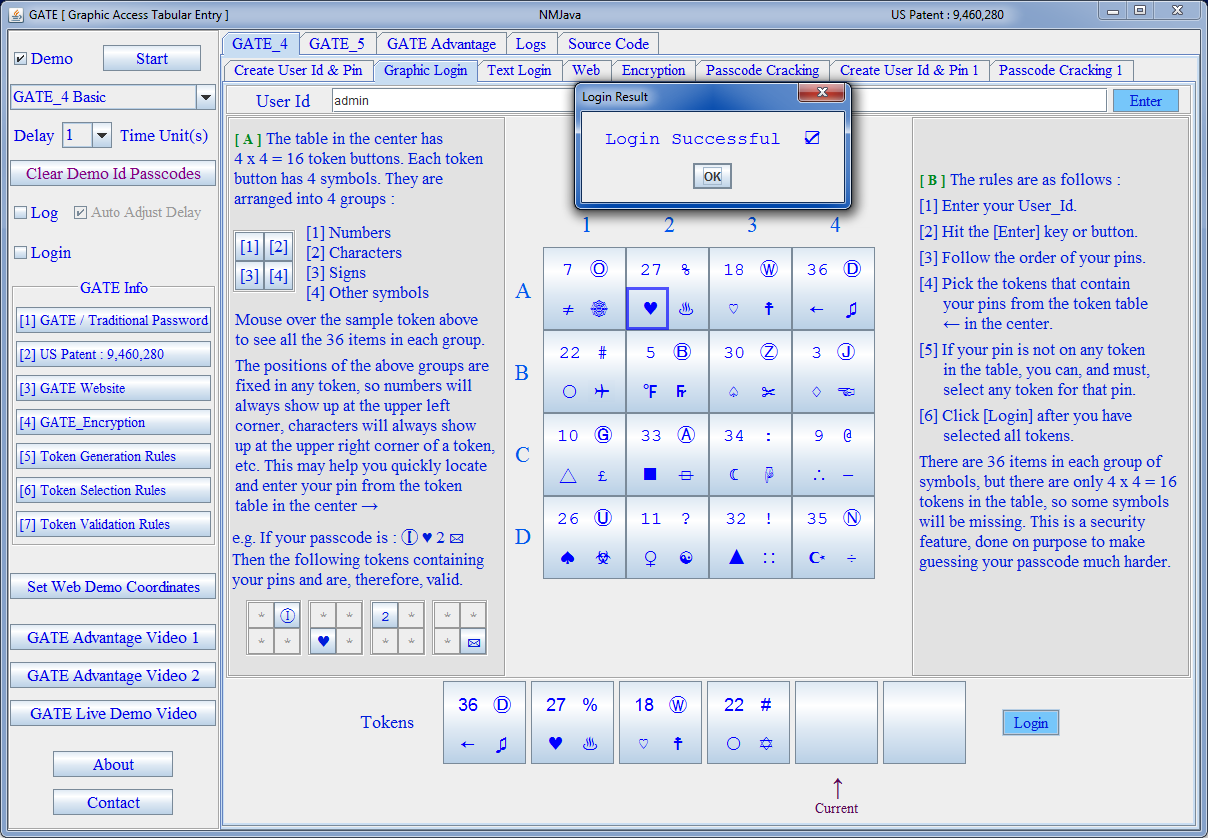
The newly patented GATE system overcomes all of the above weaknesses. Special characters are part of the GATE design. It uses tokens to let user enter user pins from passcode, each token has several symbols, some randomly selected user pins are included in these tokens. It is impossible to tell which symbols in the tokens are valid user pins, which are non-user pins. thereby increasing password strength exponentially. Some user pins might not even appear in the tokens, in that case user can and must enter random tokens in place of those pins, and this uncertainty makes guessing your passcode much harder.
This approach is like hiding a needle in a haystack. Instead of entering one digit at a time like the traditional approach, the GATE system enters multiple symbols at a time as a token. Only someone with knowledge of the passcode will be able to tell if the token entered is valid or not.
For example, if my passcode is : Ⓘ ♥ 2 ✉
The tratitional approach is to enter the following symbols one at a time : Ⓘ , ♥ , 2 , ✉
If a hacker stands next to me and watches me enter these symbols from the screen, he can easily remember the sequence and therefore steal my passcode.
But if I enter the following tokens [ each has 4 symbols ] one at a time :
| Token 1 | Token 2 | Token 3 | Token 4 |
| Key Tokens : | 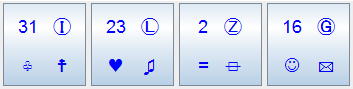 |
Then the passcode is hidden in the symbols in each token, and the hacker won't be able to tell which ones of the symbols in the tokens represent the correct passcode.
You might think, well, the passcode is still among the symbols in the tokens, and if a hacker observes enough times, he can guess which symbols in the tokens are part of the passcode. OK, that's a great observation, but see if you can figure out the passcode from the following subsequent successful login sessions :
| Token 1 | Token 2 | Token 3 | Token 4 |
| Key 1 Tokens : |  |
| Key 2 Tokens : |
| Key 3 Tokens : |
The passcode remains the same, and the above sessions are all successful login attemps with valid tokens, but the hacker may have a hard time guessing the correct passcode due to the rules of this innovative new method to authencicate users. The token are automatically generated by the new method's algorithm, and because the user and the system know the passcode, they know which tokens are valid. Since the hacker is unaware of the passcode, he will not know which ones among them are valid tokens to select. And the next time when a user logs in, the system will present a different set of tokens with randomly generated symbols in them.
In the tokens table, some user pins might not even appear, but at least one user pin will definitely be in the tokens table. When a user pin is missing in the table, user can and must enter a random token in place of that pin, and this uncertainty makes guessing your passcode much harder and therefore greatly increases passcode safety.
To simplify the explanation, here is an easy example; let's say Alice wants to authenticate Bob over a network, while Eve is eavesdropping on their communication. Anything sent from Alice to Bob, or from Bob to Alice, Eve will know.
Both Bob and Alice know that Bob's passcode is "I ♥ U". Let's call each symbol a pin. So in order to authenticate Bob, he needs to transfer these 3 pins to Alice over the network.
The traditional way is for Bob to pass the 3 pins "I" , "♥" , "U" to Alice over the network, and Eve can easily and obviously see the 3 pins in the passcode.
But Alice is clever enough not to show her communication with Bob in plain sight. Because both Alice and Bob know what Bob's pins are, Alice would present Bob with a group of tokens, generated by token generation rules, with at least one of Bob's pins in the tokens, and ask Bob to pick the correct ones to enter his pins (each token has several symbols in it).
For example, Alice can send Bob the following tokens for Bob to pick and enter his pins :
Token 1 : 3 I #
Token 2 : 5 P &
Token 3 : 9 U @
Token 4 : 6 W +
Now looking at the above 4 tokens, Bob selects the appropriate tokens to enter his pins according to token selection rules : if a pin appears in a token, he must select that token to enter the pin, but if a pin is not in any of the tokens, he can and must select a wildcard [ any ] token to enter that pin.
So Bob goes through his passcode and enters his 3 pins one by one. His first pin is "I", so he scans the above 4 tokens and tries to find a token that contains this pin, the first token [ 3 I # ] contains this pin, so he selects this token to enter his first pin.
Now Bob needs to enter his second pin "♥", but it is not in any of the tokens, so according to the token selection rules, he can and must pick a wildcard [ any ] token to enter this pin, so he selects the 4th token [ 6 W + ].
For the 3rd and last pin "U", Bob goes through the 4 tokens and finds it in the 3rd token, so he selects it [ 9 U @ ] to enter his 3rd pin.
As a result of the above selection process, Bob entered 3 tokens :
Token 1 : 3 I #
Token 4 : 6 W +
Token 3 : 9 U @
These 3 tokens will be sent over the network to Alice for validation, once Alice gets the 3 tokens entered by Bob, she will go through each one of them and see if they are valid according to the token selection/validation rules.
Alice knows that Bob's first pin is "I", so she checks all the 4 tokens she sent to Bob to see if the symbol "I" is in any of them. Since it's in the 1st token, and Bob did enter that token as the first pin, it's valid.
Then Alice looks at Bob's 2nd pin "♥". Since it's not in any of the 4 tokens that she sent to Bob, it must be entered by selecting a wildcard random token, and Bob did enter a wildcard token, so it's valid too.
For the 3rd and last pin in Bob's passcode : "U", Alice goes through all the tokens she sent to Bob and finds it in the 3rd token, and she sees that Bob did enter the 3rd token [ 9 U @ ] for that pin, therefore the 3rd pin Bob entered is also valid.
Since the tokens Bob entered are all valid, his authentication is validated. Otherwise, if any token Bob entered is invalid, or if Bob entered more or less tokens than the pin count [3] in his passcode, then he will be denied access.
But because Eve is eavesdropping on their communication, she can see the tokens entered by Bob : [ 3 I # ] , [ 6 W + ] and [ 9 U @ ], but she can not tell which symbols among them are Bob's true passcode. And if she intercepts again next time when Bob tries to login, she will get another set of random symbols, and she will still be unable to figure out Bob's real passcode.
| Comparing Traditional Password To The GATE System And Method |
| Login |
| Bob |  |
|
| Eve |  |
|
| Alice |  |
|
| Traditional [ Weak & Dangerous ] |
1st Time |
| Step 1 : |
| User Id : | Bob |
| Password : | I ♥ U |
|
→ |
| User Id : | Bob |
| Password : | I ♥ U |
|
→ |
| User Id : | Bob |
| Password : | I ♥ U |
|
| Step 2 : |
Grant Access ! |
←‐‐‐‐‐‐‐‐‐ |
[ Validate from saved records ] ⤶ |
|
| 2nd Time [ Same As 1st Time ] |
| Step 1 : |
| User Id : | Bob |
| Password : | I ♥ U |
|
→ |
| User Id : | Bob |
| Password : | I ♥ U |
|
→ |
| User Id : | Bob |
| Password : | I ♥ U |
|
| Step 2 : |
Grant Access ! |
←‐‐‐‐‐‐‐‐‐ |
[ Validate from saved records ] ⤶ |
|
| 3rd Time |
| Step 1 : |
| User Id : | Bob |
| Password : | I + U |
|
→ |
| User Id : | Bob |
| Password : | I + U |
|
→ |
| User Id : | Bob |
| Password : | I + U |
|
| Step 2 : |
Deny Access ! |
←‐‐‐‐‐‐‐‐‐ |
[ Can't validate from saved records ] ⤶ |
|
| The GATE System [ Strong & Secure ] |
1st Time |
| Step 1 : |
User Id : Bob |
→ |
User Id : Bob |
→ |
User Id : Bob ⤵ |
| Step 2 : |
| Token 1 : 3 I # |
| Token 2 : 5 P & |
| Token 3 : 9 U @ |
| Token 4 : 6 W + |
|
| ↓ |
|
← |
| Token 1 : 3 I # |
| Token 2 : 5 P & |
| Token 3 : 9 U @ |
| Token 4 : 6 W + |
|
← |
[1] Get Bob's passcode from saved records : I ♥ U
[2] Generate tokens from Bob's passcode :
| Token 1 : 3 I # | |
| Token 2 : 5 P & | |
| Token 3 : 9 U @ | |
| Token 4 : 6 W + | |
|
[3] Send the tokens to Bob for him to select his passcode pins
|
| Step 3 : |
Select tokens to enter pins in passcode :
| Token 1 : 3 I # |
| Token 4 : 6 W + |
| Token 3 : 9 U @ |
|
→ |
| Token 1 : 3 I # |
| Token 4 : 6 W + |
| Token 3 : 9 U @ |
|
→ |
Validate tokens from Bob, using saved passcode : I ♥ U
| Token 1 : 3 I # | ☑ |
| Token 4 : 6 W + | ☑ |
| Token 3 : 9 U @ | ☑ |
|
| Step 4 : |
Grant Access ! |
←‐‐‐‐‐‐‐‐‐ |
[ Send result to Bob ] ☑ ⤶ |
|
| 2nd Time [ Different Tokens ] |
| Step 1 : |
User Id : Bob |
→ |
User Id : Bob |
→ |
User Id : Bob ⤵ |
| Step 2 : |
| Token 1 : 2 X % |
| Token 2 : 4 U ! |
| Token 3 : 8 A @ |
| Token 4 : 5 W $ |
|
| ↓ |
|
← |
| Token 1 : 2 X % |
| Token 2 : 4 U ! |
| Token 3 : 8 A @ |
| Token 4 : 5 W $ |
|
← |
[1] Get Bob's passcode from saved records : I ♥ U
[2] Generate tokens from Bob's passcode :
| Token 1 : 2 X % | |
| Token 2 : 4 U ! | |
| Token 3 : 8 A @ | |
| Token 4 : 5 W $ | |
|
[3] Send the tokens to Bob for him to select his passcode pins
|
| Step 3 : |
Select tokens to enter pins in passcode :
| Token 1 : 2 X % |
| Token 4 : 5 W $ |
| Token 2 : 4 U ! |
|
→ |
| Token 1 : 2 X % |
| Token 4 : 5 W $ |
| Token 2 : 4 U ! |
|
→ |
Validate tokens from Bob, using saved passcode : I ♥ U
| Token 1 : 2 X % | ☑ |
| Token 4 : 5 W $ | ☑ |
| Token 2 : 4 U ! | ☑ |
|
| Step 4 : |
Grant Access ! |
←‐‐‐‐‐‐‐‐‐ |
[ Send result to Bob ] ☑ ⤶ |
|
| 3rd Time [ Different Tokens ] |
| Step 1 : |
User Id : Bob |
→ |
User Id : Bob |
→ |
User Id : Bob ⤵ |
| Step 2 : |
| Token 1 : 3 Y & |
| Token 2 : 1 I $ |
| Token 3 : 6 L ^ |
| Token 4 : 7 J ♥ |
|
| ↓ |
|
← |
| Token 1 : 3 Y & |
| Token 2 : 1 I $ |
| Token 3 : 6 L ^ |
| Token 4 : 7 J ♥ |
|
← |
[1] Get Bob's passcode from saved records : I ♥ U
[2] Generate tokens from Bob's passcode :
| Token 1 : 3 Y & | |
| Token 2 : 1 I $ | |
| Token 3 : 6 L ^ | |
| Token 4 : 7 J ♥ | |
|
[3] Send the tokens to Bob for him to select his passcode pins
|
| Step 3 : |
Select tokens to enter pins in passcode :
| Token 3 : 6 L ^ |
| Token 4 : 7 J ♥ |
| Token 1 : 3 Y & |
|
→ |
| Token 3 : 6 L ^ |
| Token 4 : 7 J ♥ |
| Token 1 : 3 Y & |
|
→ |
Validate tokens from Bob, using saved passcode : I ♥ U
| Token 3 : 6 L ^ | ☒ |
| [ "I" in Token 2 not selected ] |
| Token 4 : 7 J ♥ | ☑ | |
| Token 1 : 3 Y & | ☑ | |
|
| Step 4 : |
Deny Access ! |
←‐‐‐‐‐‐‐‐‐ |
[ Send result to Bob ] ☒ ⤶ |
|
The essence of the GATE system is to hide passcode and confuse potential hackers or interceptors from guessing the correct passcode. Showing below are some of the screenshots of a sample GATE software program demonstrating different functionalities of the new method.
| Create User Id & Pin |
|---|
 |
|
| Graphic Login |
|---|
 |
|
| Text Login |
|---|
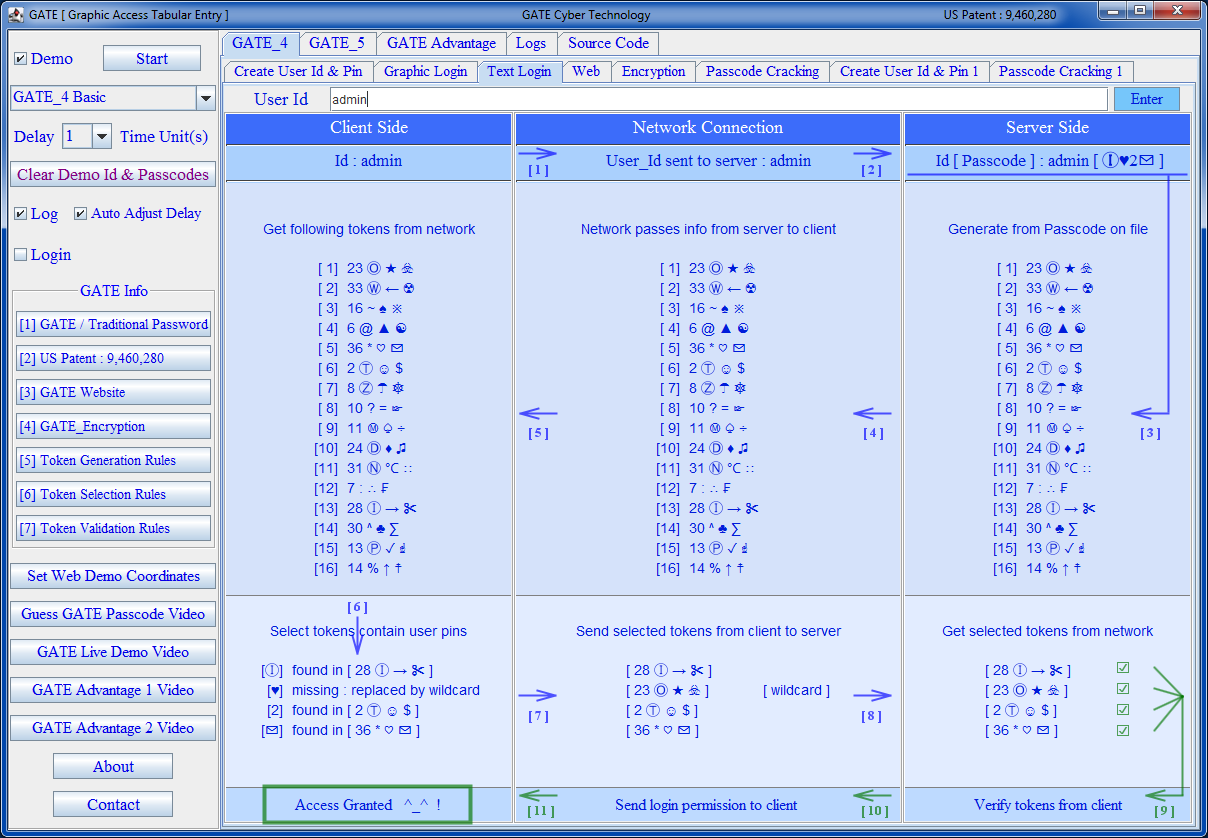 |
|
| GATE Web |
|---|
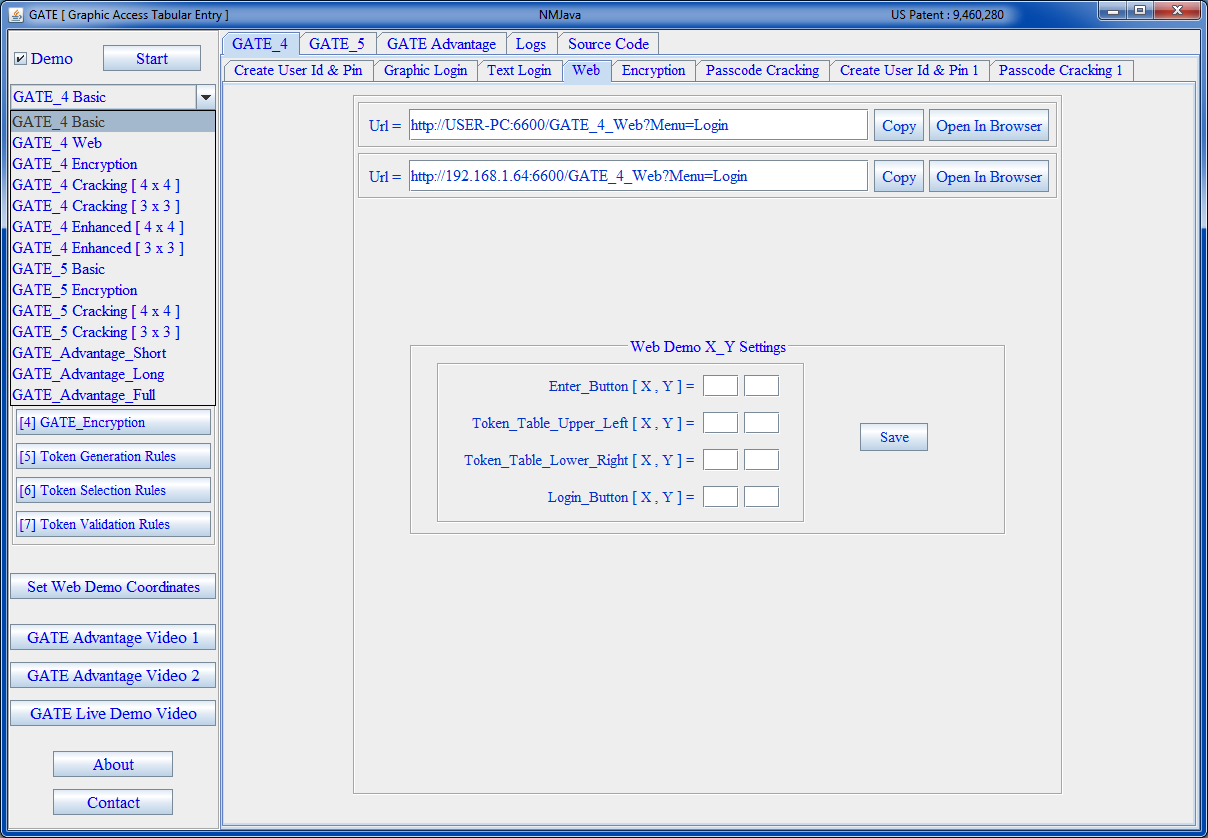 |
|
| GATE Encryption |
|---|
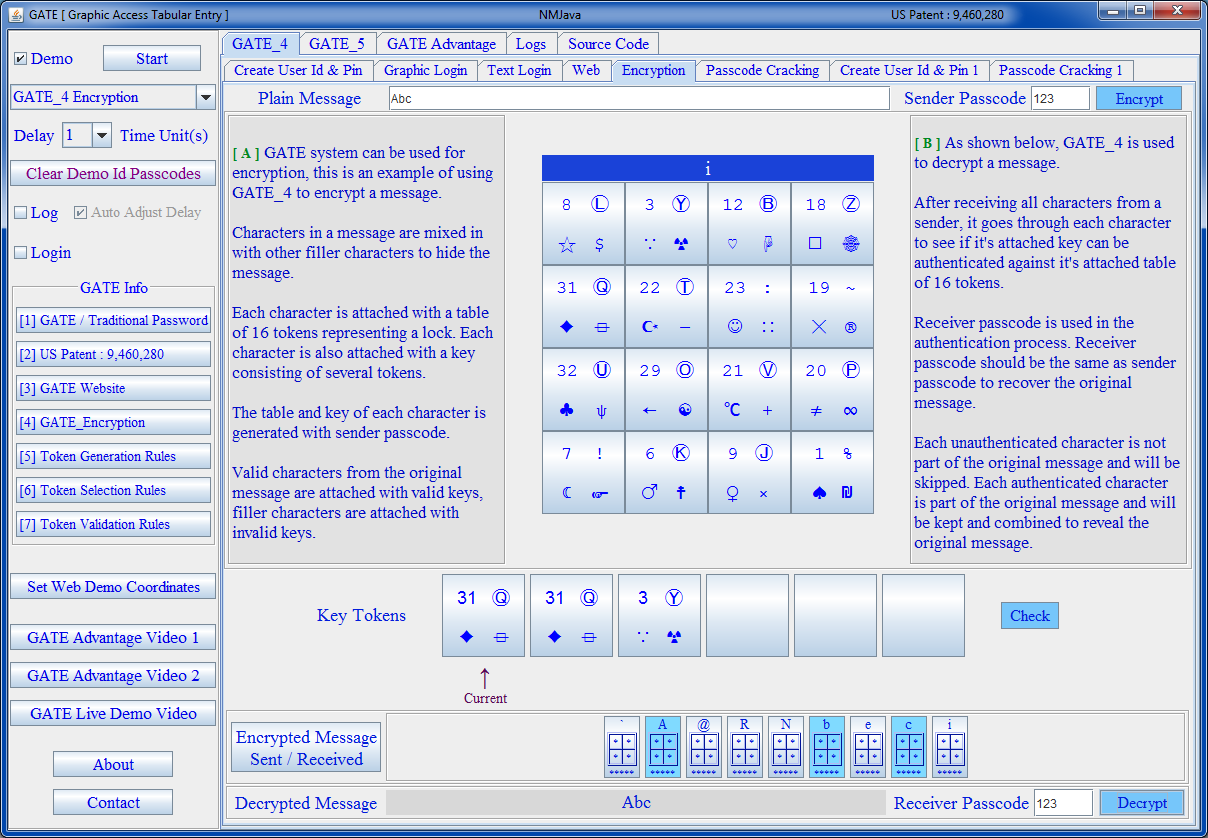 |
|
GATE vs Traditional Password
Download and play video |
|---|
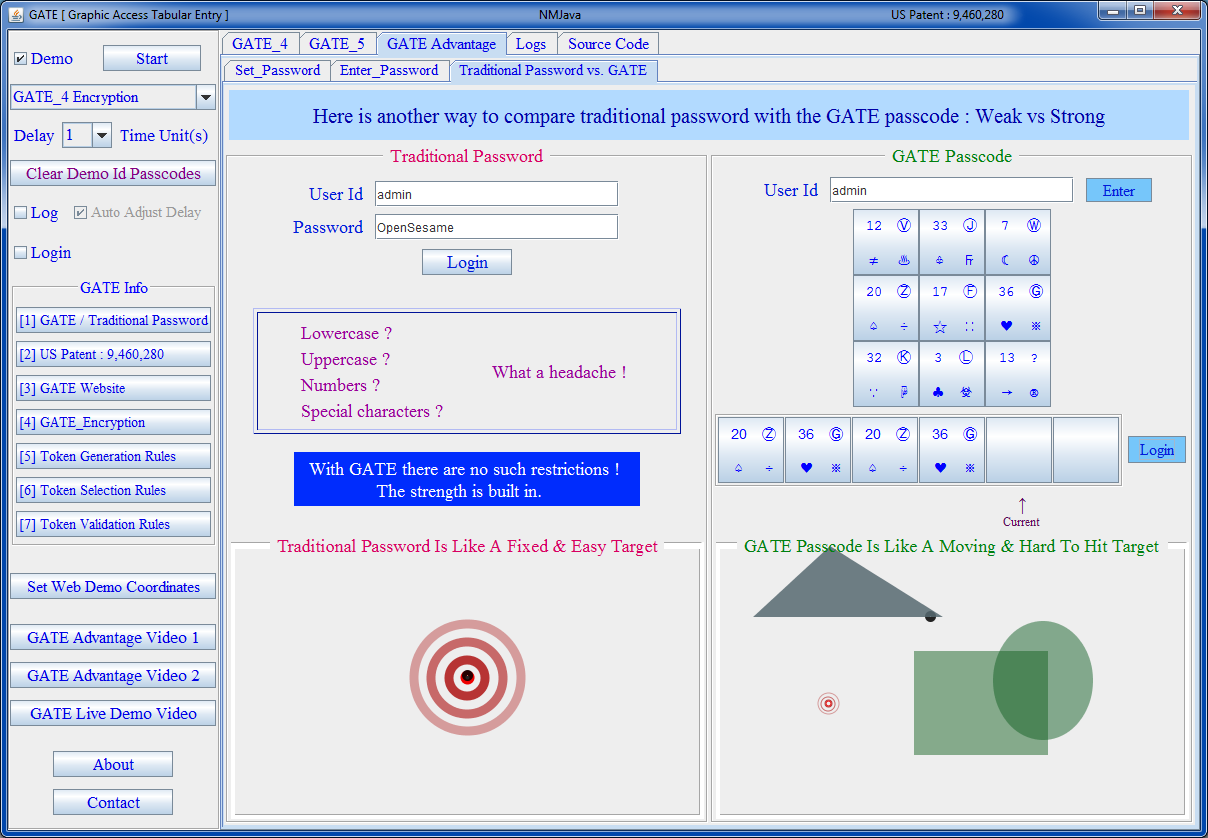 |
|
| GATE 3 x 3 [ Blue ] |
|---|
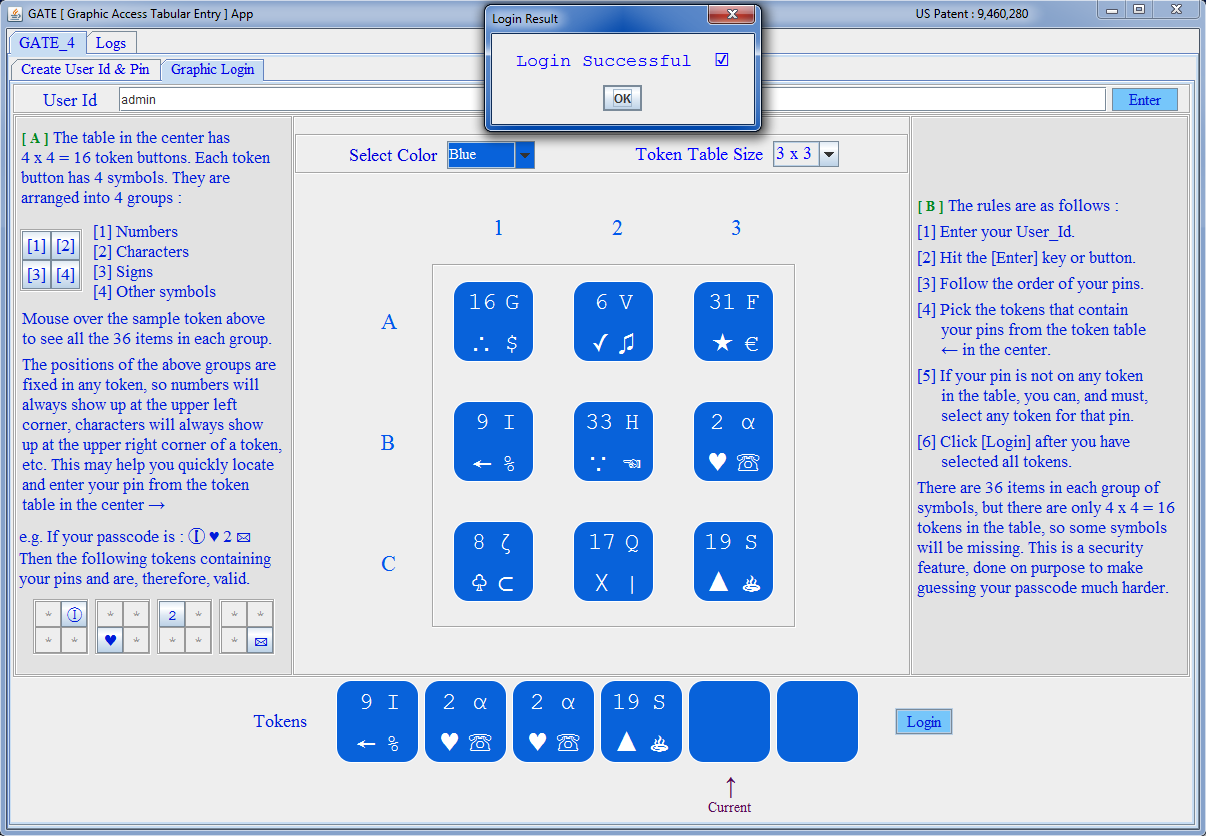 |
|
| GATE 3 x 3 [ Red ] |
|---|
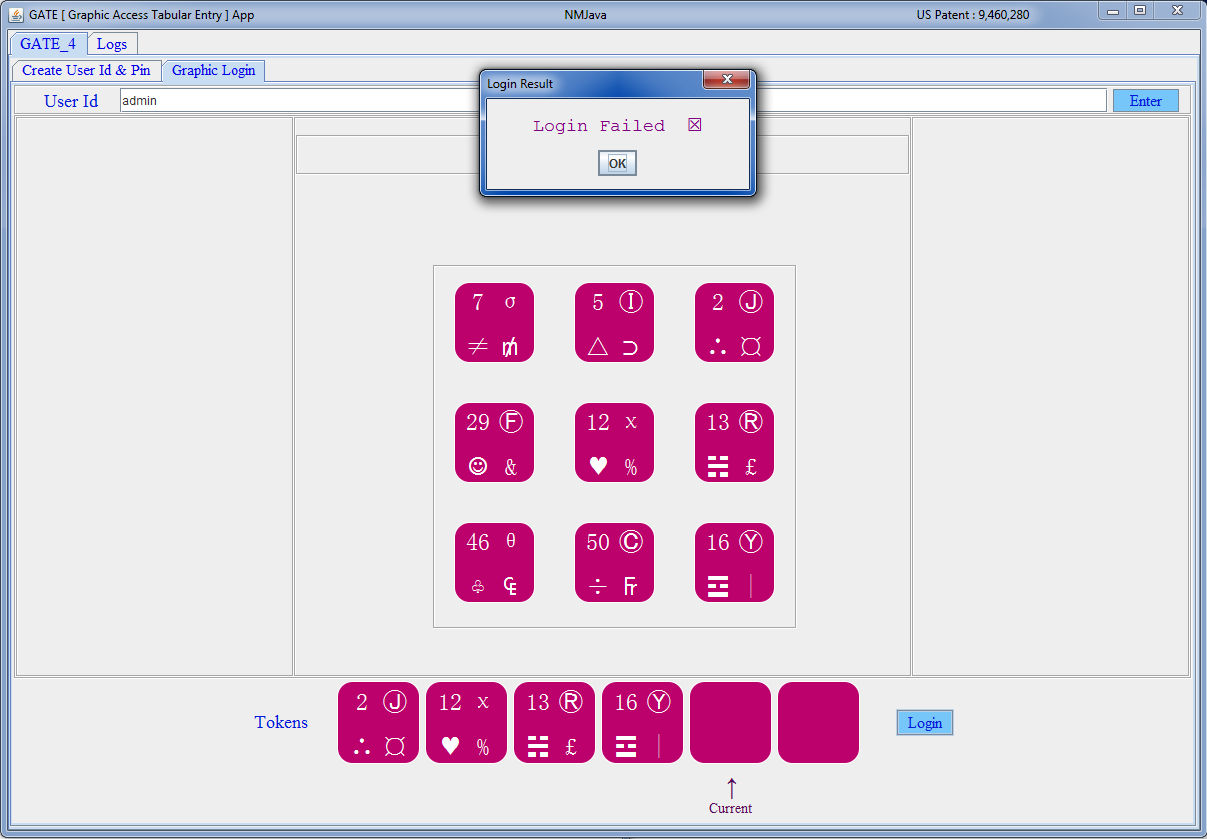 |
|
| GATE 4 x 4 [ Grey ] |
|---|
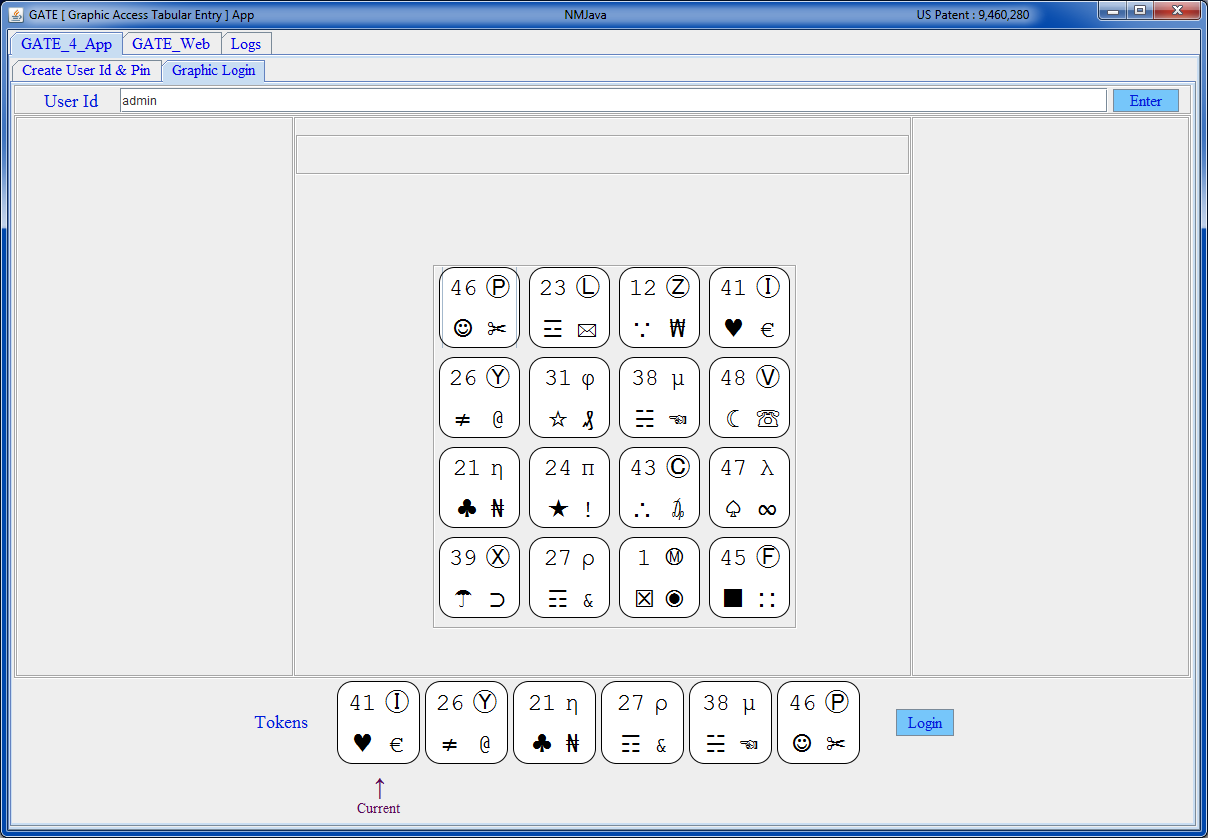 |
|
I was asked how GATE compares to other authentication systems. While finger printing, iris scanning, Yubikey and RSA tokens depends on you physically own and use something [ whether it's the print on your finger, your iris or key fobs ], and that "something" can be lost, stolen or imitated. But GATE is software based, it depends on the knowledge you have about your passcode, that's the main difference. For GATE, there is no such hardware to purchase/possess, to carry or to be stolen. The passcode is stored on the server, and it should be encrypted. Details of how to safely encrypt that file is on the FAQ page [ # 8 ].
Comparing to other authentication systems, GATE has an advantage. Iris scanning and finger printing can only be done between people and machine, while the GATE system can be used in both people to machine and machine to machine authentication. You can use GATE to program machines to authenticate each other.
The table of tokens is generated by an algorithm on the fly. When user enters the user Id, the server loads the user's passcode, and randomly picks some of the user pins [ usually not all ], to mix them with other symbols and present the custom generated table of tokens to the user, and when the same user logs in next time, the server goes through the same process again to pick another random number of pins from user passcode and mix them with another set of randomly selected other symbols and present the tokens to the user in a table, so there is no table stored on the server, and no table uploaded to the server.
The main difference is : traditional password is like a regular glass, it will shatter after just one shot [ interception ], the GATE system is like a bulletresistant enhanced glass, which can withstand dozens or hundreds of shots [ interceptions ] without breaking. Like a bulletresistant glass which is designed to be shot at, the GATE system is designed to be seen while entering the passcode without being afraid that the passcode will be stolen, therefore it is peek-resistant and interception-resistant. The weaknesses of traditional password are all overcome by the GATE system. It's time for a change to enhance cyber security, and this revolutionary innovative method will definitely give you an advantage over your competitors.
Donate For Cybersecurity !
![View Min [ Frank ] Ni's profile on LinkedIn](https://static.licdn.com/scds/common/u/img/webpromo/btn_myprofile_160x33.png)


